Better Salesforce security for remote work
Salesforce already utilizes some of the most advanced and sophisticated technology for internet security available today, and we’ve never needed it more. The system is a veritable treasure trove of any company’s most important data and that makes it target number one for would-be criminals. And they are employing some very nefarious tactics to get at your data.
Because Salesforce servers are so secure, many cybercriminals have shifted away from hacking and instead are targeting individual people in an attempt to gain access to a company’s data. And with more and more employees working remotely with weaker protocols than the office, online security is more important than ever. We’ve compiled a list of our Salesforce security best practices to employ in your organization.
Feature 1: Two-Factor Authentication
 A username and password combination is your first line of defense for protecting your Salesforce data. But, we’ve all heard unfortunate tales about how easy it can be for a password to be compromised. What’s an admin to do? Enter two-factor authentication.
A username and password combination is your first line of defense for protecting your Salesforce data. But, we’ve all heard unfortunate tales about how easy it can be for a password to be compromised. What’s an admin to do? Enter two-factor authentication.
Two-factor authentication is a method of verifying a user’s identity by adding a second layer of protection. It requires the user to not only provide something that they know (in this case, their password), but also something that they have in their possession. Salesforce has a solution for providing the second factor in the form of a free mobile app that can be installed on iOS and Android devices. When two-factor authentication is enabled, a user will be prompted to check their device and verify their login after they provide their username and password.
We take advantage of two-factor authentication for added security in our own Salesforce org at Redpath every day. Our team has found it to be a simple and unobtrusive step when we log in as well as a powerful tool to keep our customers’ data safe. This has been particularly important in this time of COVID-19 when we’ve all been forced to work from home. With two-factor identification, our productivity has remained consistent and our constant goal of maintaining client data security hasn’t missed a step.
Ready to get started with two-factor authentication? Check out this module on Trailhead for step-by-step instructions. As with any new feature, be sure to test in a sandbox and communicate, communicate, communicate with your users before deploying to production!
Watch this on-demand webinar to round out your your Salesforce org with the top security features.
Feature 2: IP Address Restrictions
Another layer of security that can prevent malicious login attempts through compromised passwords is to lock down the physical location where Salesforce logins can occur. Even though working from home has become commonplace, as long as your organization has a corporate VPN, users can be forced to be “on location” (logged in to the VPN) in order to log in to Salesforce. This is accomplished by restricting logins to your organization’s IP ranges.
IP address restrictions are set at the profile level. In Setup, open a profile and go to “Login IP Ranges” to add one or more ranges of IP addresses. Be sure to test this in a sandbox first, and make sure that your System Administrator profile is the last to be updated with IP ranges, in case the configuration needs to be adjusted after it is deployed.
What about mobile app users who are on the go? While you can enforce the same IP ranges for mobile app users, requiring mobile users to log in to the corporate VPN from their mobile device may pose a barrier to mobile adoption. If acceptable within your organization’s security standards, you can relax the IP range restrictions for mobile app users in Setup under “Manage Connected Apps.” Check out this module on Trailhead for more information about the available options.
Feature 3: Object Security and Field Classification
Security doesn’t end after a user has successfully logged in to the system. Careful consideration must be given as to what data each user should be able to access. In Salesforce, access to data can be controlled at the object, field or record level.
Access to objects is the simplest piece of data security to control. Let’s say your company collects program applications in Salesforce with the application data stored in records in a custom “Program Application” object. Because of the sensitive nature of this data, program application records should only be displayed to members of the Program Management team.
Time to do an audit of your profiles and make sure there aren’t any extra profiles with Read access to the program application object. The Enhanced Profile List View interface can make this a breeze by displaying the object-level security on that object for all of your profiles in a single list. Don’t forget to check your permission sets, too, using the same interface. If any permission sets grant access to that object, be sure to check which users are assigned.
Once you’ve finished auditing your profiles for object-level access, you should review the fields within that object. In our example, the program application object includes a field for tracking applicants’ social security numbers. Access to this field needs to be more limited within the program management team, so it is important to make sure that the field is not visible to the program management profile. A permission set should be used to provide more granular access.
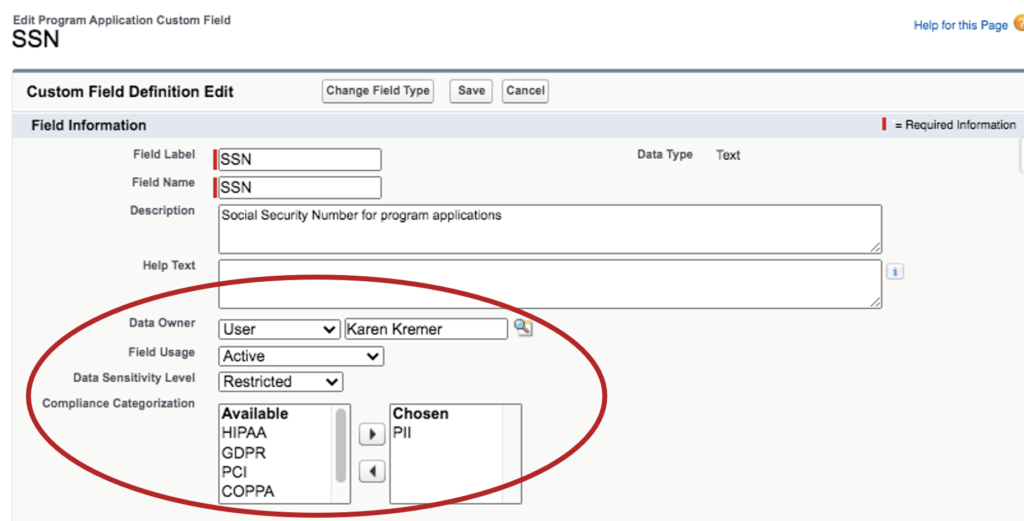
Now is also a good time to take advantage of a new feature in Salesforce (as of the Winter ‘20 release): metadata classification. This feature allows an administrator to identify fields that contain sensitive or regulated data, and to assign an “owner” to the field as the point of contact for security-related questions about the data that is being stored. By updating the classification information, admins will easily be able to identify this field as being highly regulated, and will know who to ask if they have questions about the company’s use of this data.
Feature 4: Security Health Check
Because security is so important, Salesforce provides a “health check” feature to identify potential issues with your org’s security settings. Running a health check is quick and easy. Simply go to Setup and select “Health Check,” wait a few seconds for the scan to run, and voila! You will be presented with an overall score and list of recommendations for security improvements, as seen in the example below.
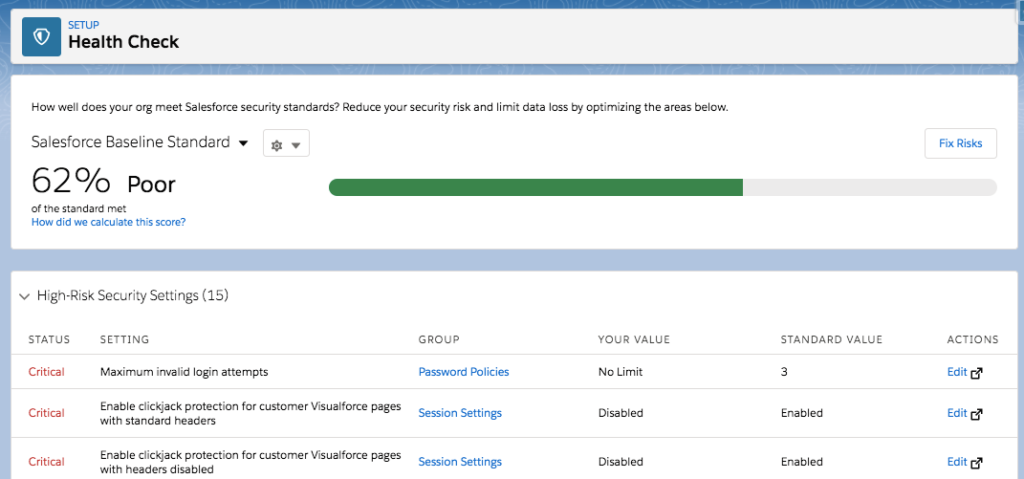
The health check score is calculated with a formula that measures how well your security settings meet the security baseline established by Salesforce. For example, changing your password expiration cadence to one year will lower your overall health check score. Increasing it to 90 days will raise your score.
Establishing Your Own Security Best Practices
Your system’s security is not only vital to your company’s overall health, it’s an essential building block that only figures to become more important in the years ahead. Now’s the perfect time to establish two-factor identification and other measures to keep your essential Salesforce org as safe as possible. Walk through more data safety best practices in this on-demand webinar.
If you would like to explore additional Salesforce security features or need help interpreting your health check results, we can help! Take our free Salesforce Risk Assessment or contact us to set up a consultation.

With the rapid evolution of technology, Salesforce solutions are ever-changing and improving features. Contact our team for up-to-date information.

